FCSC 2023 - APT Style

APT Style
Category : forensics
General description for the series
As CISO, you anticipate ~ belatedly ~ the migration of user workstations in your fleet to Windows 10.
To do this, you ask one of your collaborators to prepare an installation ISO and, given the importance of the harmlessness of this installation medium, you decide to test it. You observe strange behaviors on the newly installed machine… You then decide to dissect this ISO, in order to understand where these behaviors come from.
Please note: for these events, you only have 10 flag attempts per event.
All proofs in this series use the same file available below.
SHA256(Win10_22H2_French_x64.iso) = 6b308977cecc9b6d8aa50a8ddabdacdf01394b0819d5978141ed61862c61143f
APT Style 1/7
Difficulty: ⭐ ⭐ ⭐
States
What object triggers the malicious behavior ? The expected response is the object path.
Which group of attackers employs a similar method ? The expected format is UNCTXXX.
The final flag is in FCSC{path:UNCXXXX} format
Solve
|
|
|
|
I got an official Windows ISO to compare it with the given file :
|
|
We will look at the different files :
|
|
“install.wim” is a file used by the Microsoft Windows operating system to store a complete operating system image, including all files and settings needed to install Windows.
To extract the files from install.wim, we will have to install wimlib.
First, we will determine which image to extract from the 2 ISOs :
|
|
The given ISO contains a single Win10 Pro image, the ISO I downloaded contains 11. We will extract the install.wim from the 6th :
|
|
|
|
We will redo a diff on the new files :
|
|
We discover that it is potentially a registry key that has been modified, so we will extract it and analyze the keys.
For this I will switch to a windows machine and use : RegistryChangesView
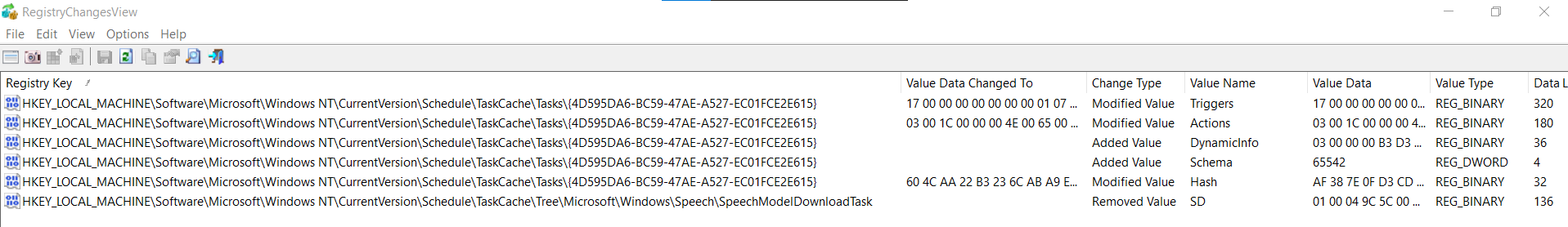
We can clearly see the keys that have been modified, added or deleted :
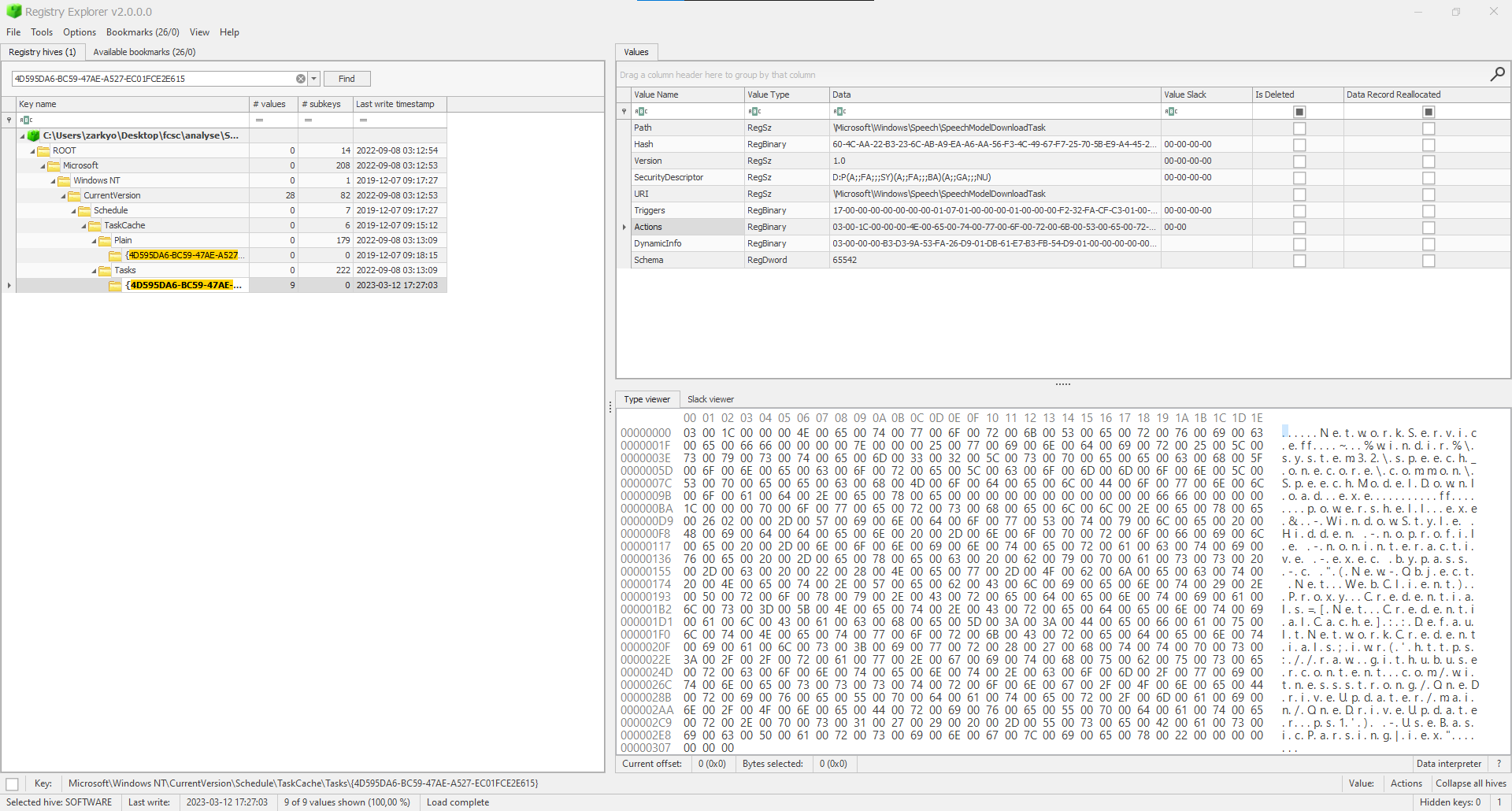
We open the hive in registry explorer to look at the values of these keys and we notice a key with a powershell command :
|
|
On the github, we can have the code of OneDriveUpdater.ps1. We also have other files (script, dll, exe) in the repository : https://github.com/witnessstrong/OneDriveUpdater
OneDriveUpdater.ps1:
|
|
We manage more or less to understand the powershell without reforming it too much.
Regarding the UNC, a little google search on ISO compromises and we arrive on this page : https://www.mandiant.com/resources/blog/trojanized-windows-installers-ukrainian-government
Flag : FCSC{HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks{4D595DA6-BC59-47AE-A527-EC01FCE2E615}:UNC4166}
APT Style 2/7
Difficulty : ⭐ ⭐ ⭐
States
What element was removed to hide this malicious behavior from Windows? The expected response is the path to the deleted item.
Which group of attackers employs a similar method? The expected response is the name of the group.
The flag is in FCSC{path:group name} format.
Solve
The only key value that is removed is the SD (Security Descriptor).
We go to the MITRE ATT&CK site to see the techniques on modifying the registry key: https://attack.mitre.org/techniques/T1112/
A hit of CTRL + f --> SD
|
|
We go to the HAFNIUM group.
Flag : FCSC{HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\Speech\SpeechModelDownloadTask\SD:HAFNIUM}
APT Style 3/7
Difficulty : ⭐
States
Which file is used as a timestomp base for malicious files ? The expected response is the full path of the file in the format: FCSC{path}.
Solve
In the powershell, we can see a piece of code that performs the timestomp change :
|
|
Just understand what the value of $ts stands for. This is equal to C:\Windows\win.ini.
Flag : FCSC{C:\Windows\win.ini}
APT Style 4/7
Difficulté : ⭐
States
What technique is used by the attacker to execute the malicious payload ? The expected response is the complete ID of the technique in the sense of the MITER ATT&CK matrix, in the format FCSC{TXXXX.XXX}.
Solve
We have the github repository with powershell scripts, an exe and in particular 2 DLLs with more or less the same name.
On the MITRE ATT&CK website, you can find this technique Hijack Execution Flow: DLL Side-Loading ; https://attack.mitre.org/techniques/T1574/002/
Flag : FCSC{T1574.002}
APT Style 5/7
Difficulty : ⭐
States
Note: it seems that the attacker deleted the malicious DLL from his online directory… The administrator who observed the malicious behavior installed it on 03/15/2023
What is the serial number of the certificate used to sign the malicious DLL? The expected response is in the format FCSC{serial number}.
Solve
We are looking for the serial number of the certificate used to sign the malicious DLL. You can get this information by going to the properties of the DLL.
We clone : https://github.com/witnessstrong/OneDriveUpdater
The version.dll DLL is not a DLL. So we do a sigcheck on verslon.dll to get the “Serial Number”. We try the flag and it does not work.
We take the statement and look at the note :
Note: it seems that the attacker deleted the malicious DLL from his online directory… The administrator who observed the malicious behavior installed it on 03/15/2023
If you want to recover an old file, you have to use WayBackMachine.
We find our repository on 03/15/2023: https://web.archive.org/web/20230315194209/https://github.com/witnessstrong/OneDriveUpdater
If you want to recover the files, you have to target an old commit: https://web.archive.org/web/20230315194218/https://github.com/witnessstrong/OneDriveUpdater/commit/575769e48d086b0e5468577a011c2322690d471a
ON downloads the DLLs:
- version.dll: https://raw.githubusercontent.com/witnessstrong/OneDriveUpdater/575769e48d086b0e5468577a011c2322690d471a/version.dll
- verslon.dll: https://raw.githubusercontent.com/witnessstrong/OneDriveUpdater/575769e48d086b0e5468577a011c2322690d471a/verslon.dll
We retrieve the “Serial Number”:
|
|
|
|
The malicious DLL is version.dll, it had been deleted and replaced by another file.
Flag : FCSC{43bb437d609866286dd839e1d00309f5}
APT Style 6/7
Difficulty : ⭐
States
Note: it seems that the attacker deleted the malicious DLL from his online directory… The administrator who observed the malicious behavior installed it on 03/15/2023
Which machine is targeted by the malicious payload? The expected response is the machine name in FCSC{name} format.
Solve
A string is enough to obtain the name of the targeted machine :
|
|
Flag : FCSC{DESKTOP-3BY599R}
APT Style 7/7
Difficulty : ⭐ ⭐
States
Note: it seems that the attacker deleted the malicious DLL from his online directory… The administrator who observed the malicious behavior installed it on 03/15/2023
Which C2 is contacted by the malicious payload? The flag is in FCSC{IP:PORT} format.
Solve
To retrieve information from C2, we will perform a dynamic analysis by running the OneDriveStandaloneUpdater.exe and analyze capture / analyze network traffic with Wireshark
Warning: it is necessary to put the correct hostname to the VM for the payload to be triggered

We directly notice port 1337, a reference to leet speak, from English “elite speak”.
Flag : FCSC{192.168.56.1:1337}