BreizhCTF 2023 - The Lost Key

Contents
The Lost Key
Difficulty: Easy
Author: Zeecka
States
The USB key of a Norman terrorist has been recovered. Investigate his support to prevent him from taking action!
Solve
|
|
A file & fdisk to get information about the dump :
|
|
|
|
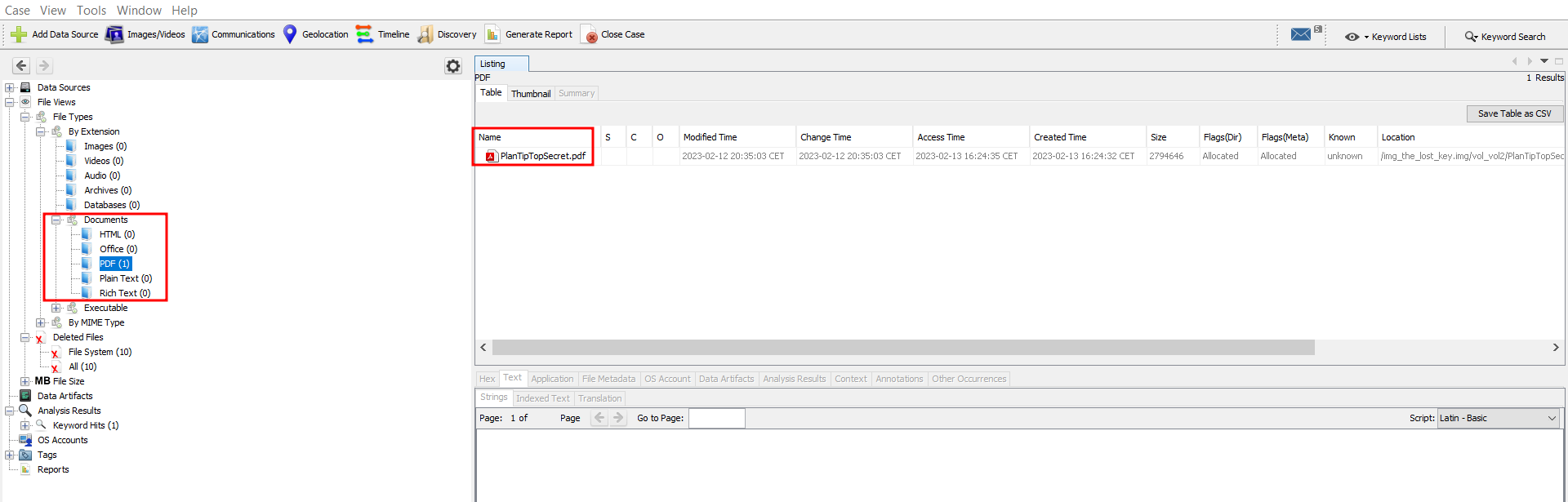
We will open in Autopsy the dump, the dump does not contain many documents. We can recover a PDF with a rather interesting name protected by a password :
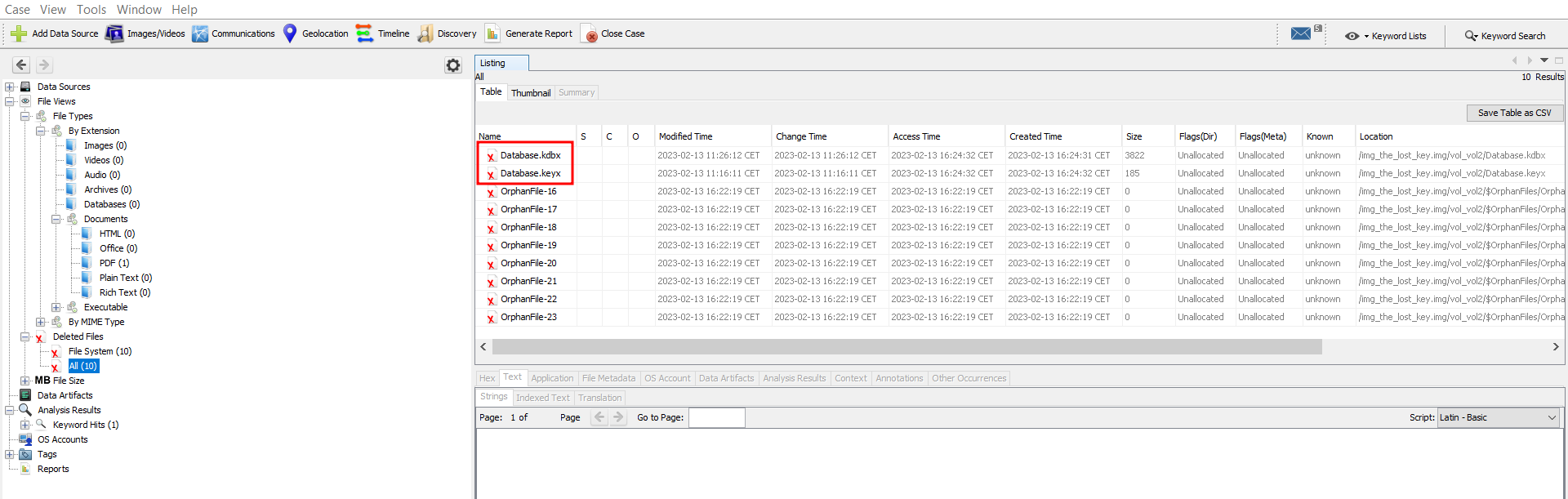
In the deleted files, we have a DB Keepass and its master key :
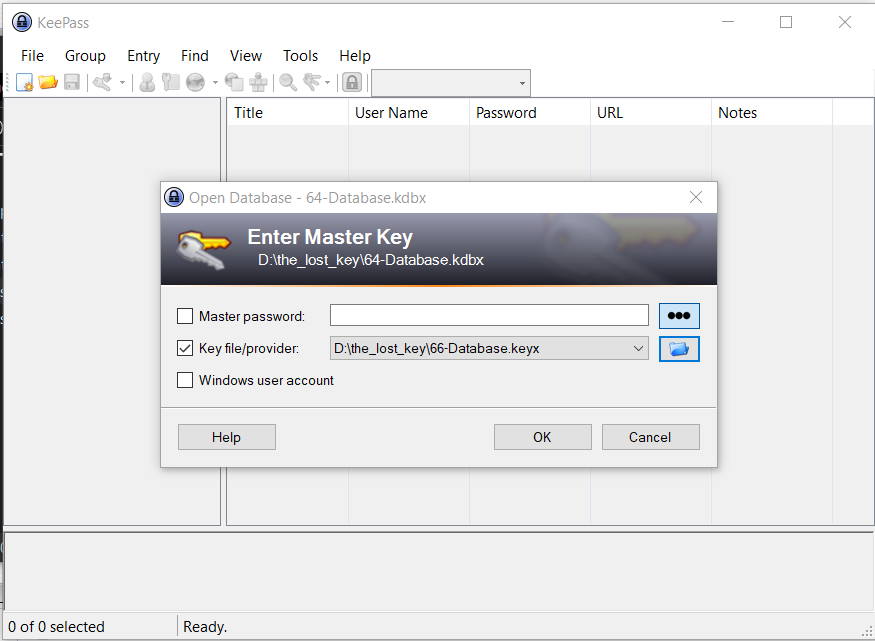
We open the keepass :
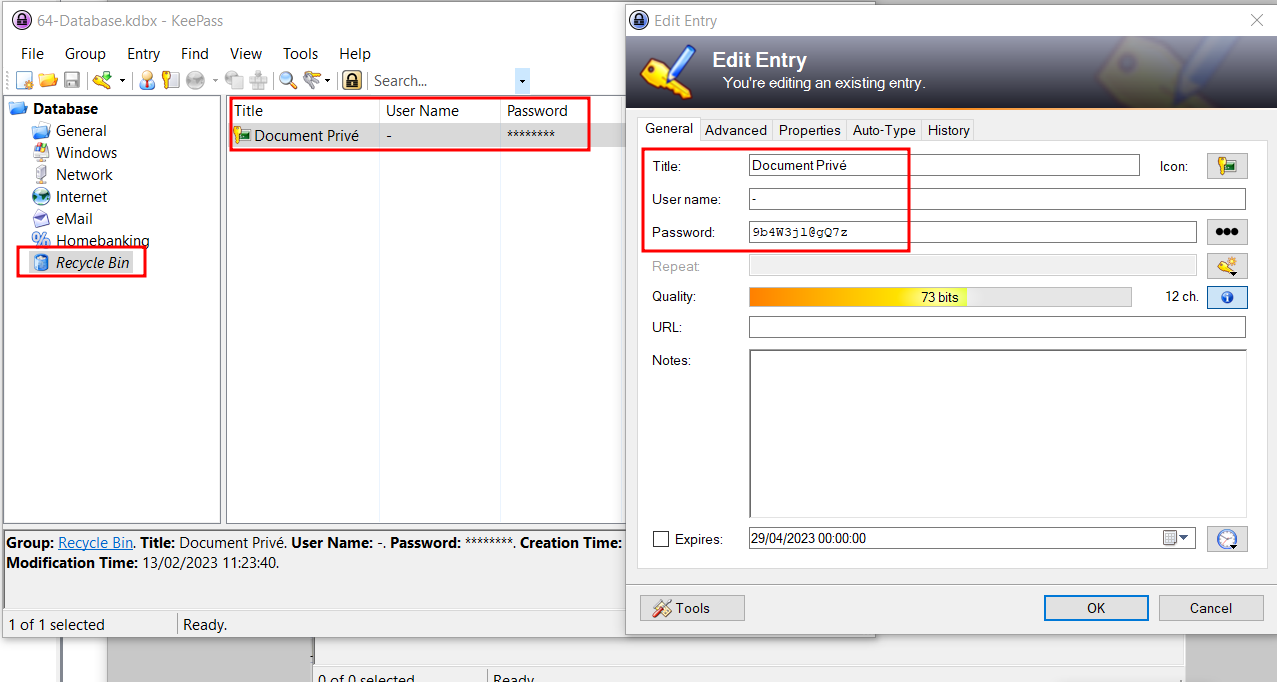
In the trash, we discover the password of the PDF :
We open the PDF document with the password and we have the flag :
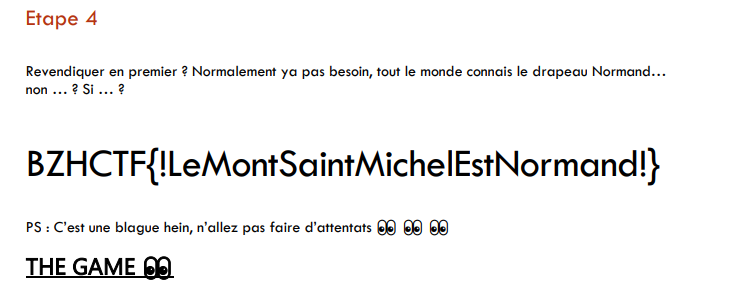
Flag : BZHCTF{!LeMontSaintMichelEstNormand!}